-
 YOUR DOCUMENTATION
YOUR DOCUMENTATION
IS NEVER MISPLACED
OR DELAYEDFIND OUT NOW HOW WE
HELP COMPANIES LOWER RISK

Too many companies rely on paper or spreadsheets to manage their safety program. Paper gets lost, or sits in a truck or at a worksite for weeks before reaching the office to be processed and assessed. And, keeping spreadsheets current and meaningful across a company is administratively intensive, difficult, and frustrating.
The alternative to paper and spreadsheets is safety management software. However, most applications are hard to use, difficult to integrate, take a long time to customize, and expensive.

With our program your Incident Reports, Hazard Reporting, Training, Inspections, and Corrective Actions are electronic, never is your documentation misplaced or delayed, your safety processes are defined giving you complete visibility into the safety of your company.
As a result incidents decrease, insurance costs remain competitive, and you can easily demonstrate that your company operates safely when bidding for the next job.
The 4 main benefits of using our software are




Use our system to:
- Conduct Job Hazard Assessments (JHAs) and create a library accessible online and offline
- Complete Field Level Hazard Assessments (FLHA).
- Relate JHAs to positions and automatically calculate overall position risk
- Document worksite and equipment inspections and assign remedial tasks
- Reference JHAs reviewed and signed off on during field level risk assessments
- Track leading and lagging indicators
- Automatically send notifications to other responsible people within the company
SOFTWARE FAQs
What is your software?
Our software is a private cloud service based on our proprietary RPM application. It is web-based and stores data in an individual database for each subscriber.
Why should I use your software?
Managing an organization’s training is a difficult and complex task. For example, think of an employee in your company. Got one? Good. Now…
- Would you be able to inform a supervisor what that employee’s current training role or roles are?
- How complaint that employee is according to the training requirements for that training role or roles?
- Or, which employees need to update their first aid requirements in 3 months? 6 months? Or 9 months?
If you can answer these questions in under a minute using your current system for every employee, training role, or training requirement in your company you can stop reading, unsubscribe, and tell your boss you deserve a raise!
If you can’t, contact us
How many servers do you have?
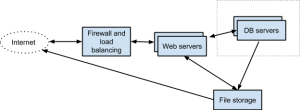
- We have multiple servers. Some are web servers that host the RPM application, and some are database servers. The number of servers is adjusted based on our operational load.
- Traffic is distributed among the web servers based on load and availability.
- The database servers are in a private network accessible only by the web servers and through VPN.
- File and email attachments are stored using an object storage service.
- For security reasons we do not share hardware details about our servers or the exact number of machines.
- Users only interact with the web servers, never the database or file servers directly. For file attachment download we provide temporary pre-signed URLs to access specific files directly from the file storage.
What are your servers? What technology do they use?
We use Microsoft technology including Windows, SQL Server, the .Net Framework, C#, and IIS.
- We are continually upgrading our servers with the current stable version and the best available hardware. We keep up with all security patches. We never use beta code.
- For security reasons we do not share more specific software or configuration details about our servers.
Where are your servers located?
- All data and files are physically located only in Canada.
- Our hosting provider is Amazon in their Montreal region.
- Amazon AWS compliance information: https://aws.amazon.com/compliance/programs/
What is your backup?
- Each of our multiple database servers keeps its own hourly backups.
- The hourly backups are kept on each server for 1 week.
- Each hourly backup is copied to a separate storage service and kept for 8 weeks.
How is your security tested?
- We perform manual and automated recursion and manual testing on every version of RPM we develop. We perform security testing on our live servers using Netsparker.
- Our application architecture makes cross-site scripting and SQL injection attacks easy to protect against. By default all input received by the web servers is scrubbed. Values are then further checked at the single point of communication between the application and database servers.
Does RPM use third party code?
Other than the Microsoft technology stack we use very little third party software. The little third party code we do use is vetted and updated. No third party code has access to the databases. We never use beta code.
What are some example software security practices?
- RPM requires a 128bit SSL connection, just like online banking
- RPM does not store plain-text passwords
- RPM does not require the client to have Java or Flash
Can we export our data?
- During your subscription your live data is available as Excel downloads by users and through the API for automated backup or synchronization.
- If ending a subscription or a large project we can create a handoff data dump that includes process fields and file attachments. The process fields in the dump are in a SQL database format.

